Everyone in industry is concerned with Industrial Network security, and our approach at PI has evolved to address this concern. In the early days, PI recommended a Defense in Depth strategy, and on top of that, we required every device passing through the test lab for certification to undergo a so called “Netload Test”. This is where we subject the device to a flood of network traffic simulating a Denial-of-Service attack making sure devices not only degraded gracefully but recovered automatically.
But now, the market is calling for additional levels of security, so we are looking beyond Netload and have come up with 3 security classes that are scalable. Class 1 is where we tighten up security for the DCP and SNMP protocols, and we protect GSD files. Class 2 is where we use authenticity between controllers and devices to ensure devices are allowed to talk to each other. This helps prevent man-in-the-middle attacks. Class 3 is where we encrypt the real-time IO data in case you are concerned it contains sensitive information like recipes, formulas, or some other trade secret.
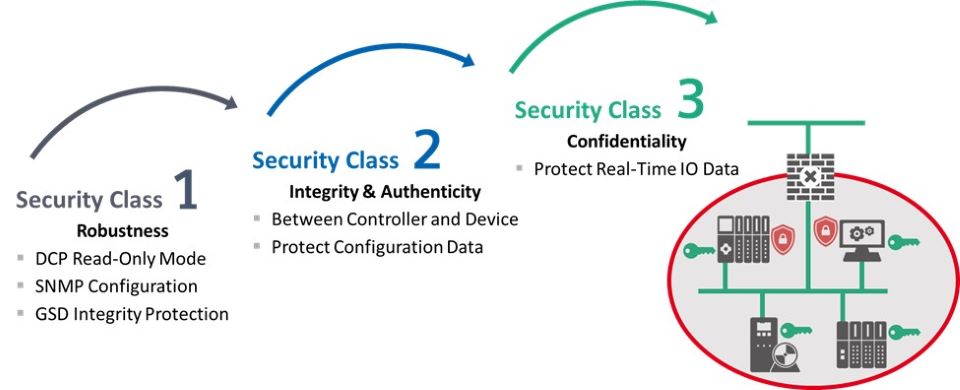
What you need to know is that Security Class 1 is ready and available for use. Devices are migrating to using DCP in Read-Only Mode and having SNMP off by default. GSDML files can now be secured, and Engineering Tools are starting to support their use.
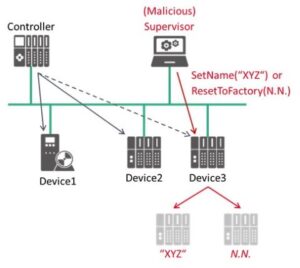 Let’s take a look at Security Class 1 in a little more detail starting with the DCP protocol. The DCP protocol is essential for 2 things – detecting PROFINET devices on the network and providing basic configuration of those devices. The issue is, DCP commands can change a device’s configuration during normal operation either by some unintended action or by some bad actor. By putting DCP in “Read-Only” mode during normal operation – a bad actor can’t rename it and try to disrupt or take over the network.
Let’s take a look at Security Class 1 in a little more detail starting with the DCP protocol. The DCP protocol is essential for 2 things – detecting PROFINET devices on the network and providing basic configuration of those devices. The issue is, DCP commands can change a device’s configuration during normal operation either by some unintended action or by some bad actor. By putting DCP in “Read-Only” mode during normal operation – a bad actor can’t rename it and try to disrupt or take over the network.
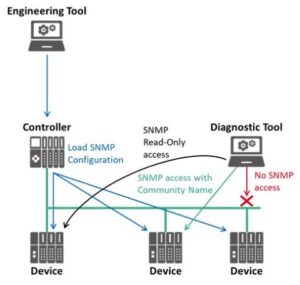 The next Security Class 1 topic is SNMP … Here we disable SNMP by default for all devices in a PROFINET network. But since SNMP can be a useful network management tool, we don’t want to completely restrict its use – we just want to make sure the network is secure by default. So, we allow SNMP access by having the Engineering Tool send SNMP configurations for all devices to the Controller. Then, the Controller provides each device its SNMP configuration when communication is established. A device can have 1 of 3 levels of configuration:
The next Security Class 1 topic is SNMP … Here we disable SNMP by default for all devices in a PROFINET network. But since SNMP can be a useful network management tool, we don’t want to completely restrict its use – we just want to make sure the network is secure by default. So, we allow SNMP access by having the Engineering Tool send SNMP configurations for all devices to the Controller. Then, the Controller provides each device its SNMP configuration when communication is established. A device can have 1 of 3 levels of configuration:
- The first level keeps SNMP access completely disabled,
- The second level allows SNMP access in Read-Only mode.
- And the third level allows SNMP access in Read/Write mode using SNMP’s Community Name authentication service.
This allows Diagnostic Tools to access devices using 1 of these 3 levels of configuration.
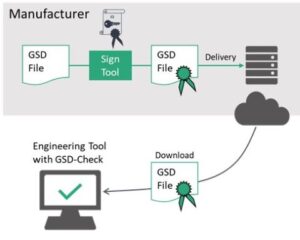 The last Security Class 1 topic is GSD integrity protection. “Integrity Protection” simply means signing GSD files so you can be sure it was supplied by the device manufacturer and hasn’t been corrupted along the way by some bad actor. To ensure integrity, manufacturers sign their GSD files and provide these protected versions to their customers. When a customer uses a GSD file, the Engineering Tool ensures it was properly signed. If it was, the GSD file is used; otherwise, the GSD file is rejected. It’s really that simple.
The last Security Class 1 topic is GSD integrity protection. “Integrity Protection” simply means signing GSD files so you can be sure it was supplied by the device manufacturer and hasn’t been corrupted along the way by some bad actor. To ensure integrity, manufacturers sign their GSD files and provide these protected versions to their customers. When a customer uses a GSD file, the Engineering Tool ensures it was properly signed. If it was, the GSD file is used; otherwise, the GSD file is rejected. It’s really that simple.
Again, these security classes are scalable with Security Class 1 ready for prime time today. Be on the lookout for Security Class 2 and Class 3 to be available within the next year or so.
