Security is becoming an increasingly important topic for machine builders and plant operators. Standards such as IEC 62443, among other things, set requirements for system security and security levels. The objective is to strengthen industry’s cyber resilience, above all on the OT level too. For this is affected by attacks on the IT level with increased regularity, effectively as “bycatch”. At the same time, it should also be protected from direct attacks, which occur in the production environment. Security is therefore a topic that not only concerns the individual system parts, but above all the communication platform used too.
Plants in automated production or the process industry are made up of numerous individual machines. The management initiates digitalization projects such as process optimization, increasing process transparency, energy management, etc. As a result, the requirements for network communication and its security change. As matters currently stand, IEC 62443, Part 3-3 (“System security requirements and security levels”) will also be incorporated in the EU Machinery Regulation via Annex III 1.1.9 and will create the circumstances for secure communication. Regardless of this, the Directive’s regulations are already helpful requirements for ensuring security in an OT network. It can be assumed that plant builders and operators will soon be required to have more network know-how. Or they will bring in external expertise, as is the case for mechanical engineering.
Security Concepts
OT security is not something that can be simply “pulled on” after completion of a plant. Rather, the topic affects every installed component of the plant and extends to the depth of the physical network structure. Cyber security must therefore be planned from the outset. To this end, IEC 62443 provides various security concepts, which not only concern the hardware and systems used, but also processes in the company and the organization’s degree of maturity, in other words, the employees’ understanding of the existing processes and their ability to know what to do in the respective problem case.
The network experts of Indu-Sol have been dealing with the reliability of industrial networks since the company was founded a good twenty years ago. Rogèr Costa at Indu-Sol, explains: “A network that does not function reliably, for whatever reasons, always also influences the security of the whole plant. We can use tools to make transparent what is going on in the network. Above all in relation to the security of networks, we can support plant builders and operators in the areas of hardware and systems as well as the maturity of the organization by providing appropriate system training courses.”
Network in the Plant Life Cycle
Whoever plans for OT security in plants should also do the same for the network. But this is a complex undertaking, which cannot be simply dealt with as an aside. It needs a network engineering expert, not only for the plant planning but also during subsequent operation. But this is usually not feasible from a financial point of view, and due to the shortage of skilled personnel, well-trained employees for network engineering are hard to find. This is where it can make sense to outsource the network topic to external service providers from the initial period of the plant’s life cycle. This provides the additional advantage that, on handover of the finished plant from plant builder to plant operator, there is no change in responsibility for the network engineering.
Network experts can provide advisory support during the strategic planning phase. They then undertake the network planning in the implementation and performance requirements period. During the setting up and commissioning they take care of the network acceptance, during operation they ensure condition monitoring and predictive maintenance through appropriate service level agreements. They are also there to provide advice for plant retrofits and help with network modifications. All these tasks need three things: Know-how, the right hardware, and services suitable for the respective period in the life of the plant.
Tools with Integrated Expertise
The times in which OT networks were still islands independent from the rest of the world are largely in the past. The advantages that can result from convergent networks and direct access to the smart sensor data of the machines and plants are too great. Therefore, OT networks are increasingly internally linked to the IT level.
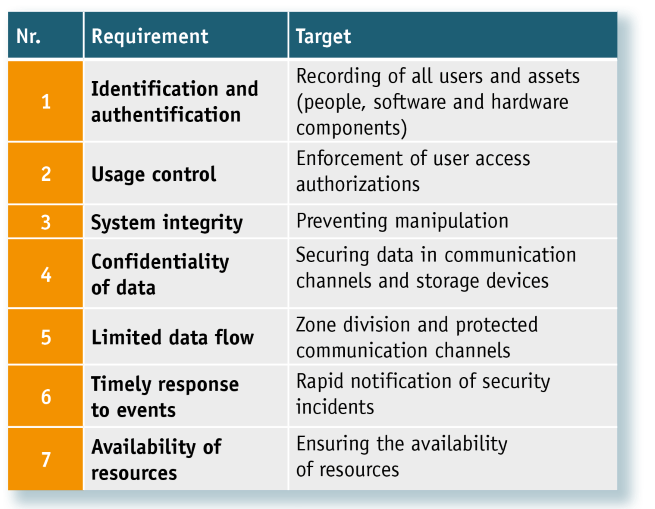
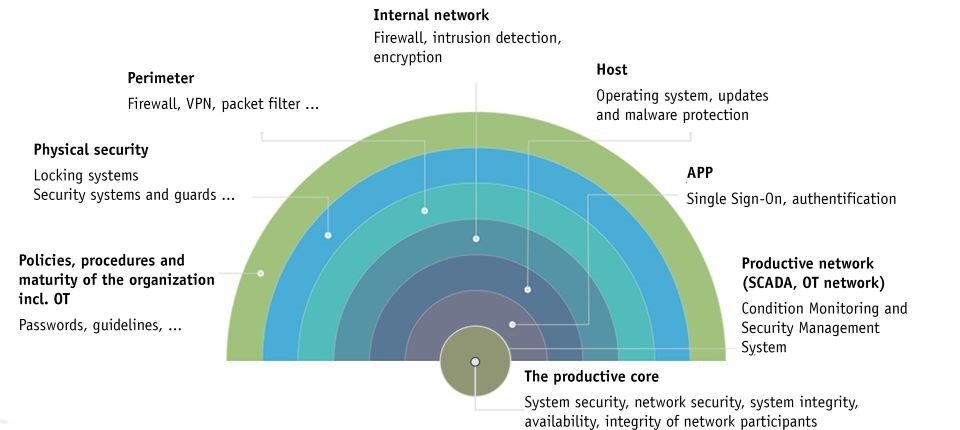
To ensure OT security, IEC 62443-3-3 sets various requirements, which ultimately provide the condition for the principle of “Defense in Depth” as shown in the figure below. The requirements relate to identification or authentication, use control, system integrity, confidentiality of the data, prompt response to events and the availability of the resources. Each of these seven requirements needs different tools or measures to implement them. Here are a few examples: An initial topology scan for the identification or authentication of OT networks and a periodic scan, for example, can be implemented and managed with a condition monitoring & security management system. The tools of the network experts check the data communication for unwanted changes, use encryption methods for secure data transmission, segment individual network areas for security reasons, ensure continuous data monitoring and automated alerting or help with the backup and restoring of device configurations.
“The list of requirements and how they can be met with our system is long”, explains Costa. “However, one trend is clear: With the requirements of IEC 62443 and the new Machinery Regulation that will soon come into effect, in future greater focus will be placed on the OT security of industrial communication networks (see table below). This requires solutions in the form of components, supporting systems as well as skilled employees or service providers with the appropriate know-how. We contribute this know-how on an equal footing within the scope of an OT competence partnership. The good news is that it is not necessary to reinvent the wheel, but instead, tried and tested solutions are on hand to face these new requirements confidently.”